In most cases, the infrastructure components (vcenter, esxi, nsx, etc.) reside on the same network. Then they communicate with each other within the same subnet without having to cross routers and firewalls.
Normally this is the case … but if you operate within large enterprise it is likely that there are management clusters that manage other clusters dedicated only to workload.
These clusters can reside on networks separated by different Layer3 (router) or Layer 4-7 (firewall) devices. In this case it is necessary to communicate with network specialists to ensure full visibility between all the objects of the infrastructure.
You will hardly have a visibility of the type any any permit , you are more likely to have to provide a detailed list with source and destination addresses and ports TPC / UDP on which to allow access.
Have you ever had to provide this list of addresses and ports? To me yes and I can assure you that it is not as simple as it seems, the objects to communicate are many and on different services, forgetting some rules can result in a lot of time spent in troubleshooting 🙁
Things have changed over the years and now it is no longer necessary to search the installation manuals for lists with all the necessary ports.
Thanks to vmware who realized this very useful website VMware Ports and Protocols 🙂
Take some time to browse through all the vmware products, you will realize how many services and ports are necessary to make the various solutions communicate.
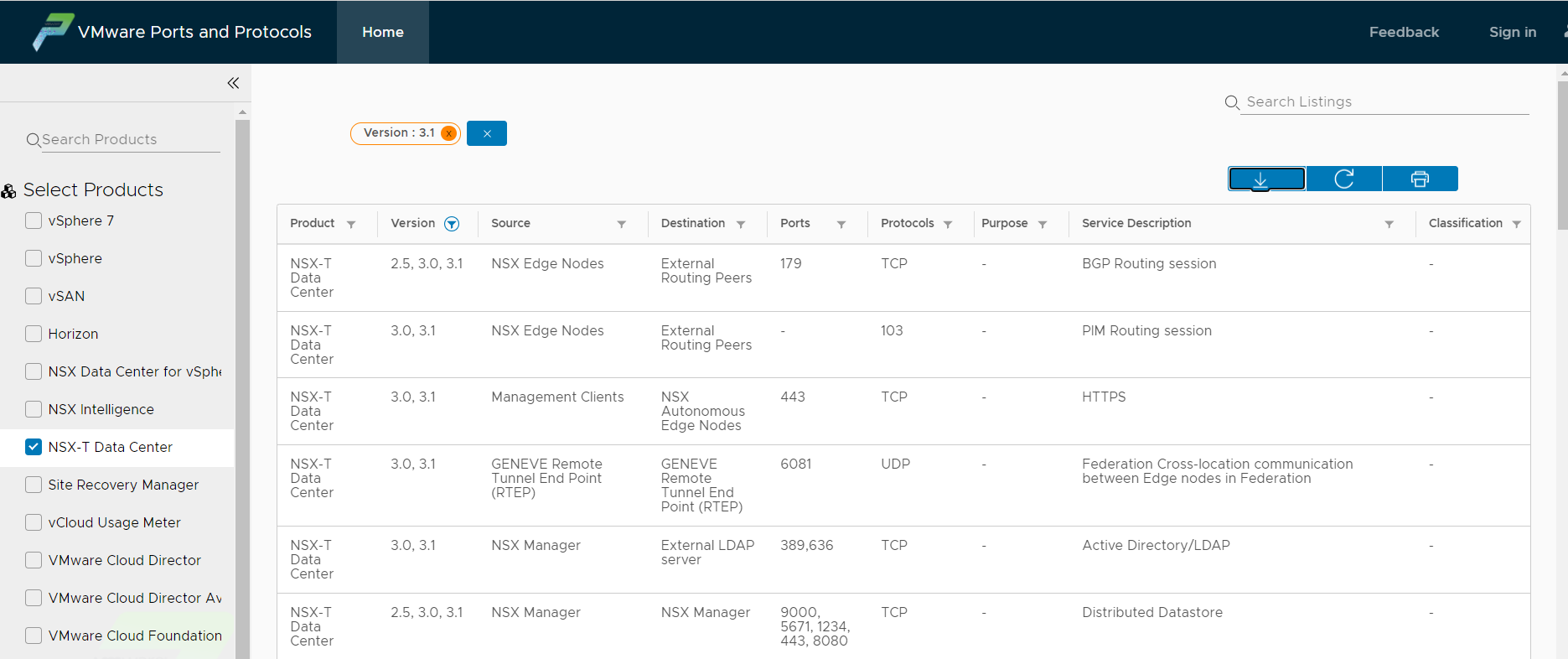
But go ahead! In this article, we’ll just find out which ports are needed for NSX-T! From the homepage of the previous site we select NSX-T Data Center.
It is possible to apply filters and select the rules by version and specific object.
Once the filters have been applied, it is also possible to export the list in pdf and excel 🙂
By filtering with version 3.1 and source Manager we obtain the list of rules needed by NSX Manager to communicate with all the objects it needs.
I summarize them below, the source is obviously the NSX Managers ip:
| Destination | Protocol | Port | Service Description |
|---|---|---|---|
| External LDAP server | TCP | 389,636 | Active Directory/LDAP |
| NSX Manager | TCP | 9000, 5671, 1234, 443, 8080, 1235, 9040 | Distributed Datastore Install-upgrade HTTP repository NSX messaging Distributed Datastore |
| KVM and ESXi host | TCP | 443 | Management and provisioning connection |
| vCenter Server | TCP | 443 | NSX Manager to compute manager |
| Traceroute Destination | UDP | 33434-33523 | Traceroute (Troubleshooting) |
| Intermediate and Root CA Servers | TCP | 80 | Certificate Revocation Lists (CRLs) |
| Syslog Servers | TCP/UDP | 6514, 514 | Syslog |
| SNMP Servers | TCP/UDP | 161, 162 | SNMP |
| NTP Servers | UDP | 123 | NTP |
| Management SCP Servers | TCP | 22 | SSH (upload support bundle, backups, etc.) |
| DNS Servers | TCP/UDP | 53 | DNS |
| Public Cloud Gateway (PCG) | TCP | 443 | NSX RPC channel(s) |
| github.com | TCP | 443 | Download IDS Signature from Trustwave Signature Repository. |
Same applies for Transport nodes and ESXi
| Destination | Protocol | Port | Service Description |
|---|---|---|---|
| Intermediate and Root CA servers | TCP | 80 | Certificate Revocation Lists (CRLs) |
| NSX Manager | TCP | 1234, 8080, 1235, 5671, 443 | NSX Messaging channel Install and upgrade HTTP repository Management and provisioning connection |
| Syslog Servers | TCP/UDP | 6514, 514 | Syslog |
| NSX-T Data Center transport node | UDP | 3784, 3785 | BFD Session between TEPs, in the datapath using TEP interface |
| GENEVE Termination End Point (TEP) | UDP | 6081 | Transport network |
NOTE : these are the ports needed by NSX, ESXi hosts will clearly need other ports for normal operation (NPT, DNS, SSH, etc.)
Some rules may seem redundant but remember that you have to distinguish between objects that start the session and their destinations, sometimes you need rules that allow traffic on both sides on the same ports.
For version 3.1 the list is of about 50 services, have a look … to know them allow you to save time 🙂